In today’s digital landscape, security is paramount. Whether you’re an individual user or managing a server, safeguarding your systems against unauthorized access is essential. One critical area to focus on is securing SSH (Secure Shell) access, which is commonly targeted by malicious actors due to its role in providing remote access to servers.
To bolster your SSH security, one effective tool you can implement is Fail2Ban. Fail2Ban is an open-source intrusion prevention framework that works by monitoring log files for suspicious activity and automatically banning IP addresses that exhibit malicious behavior. By integrating Fail2Ban into your system, you can add an extra layer of defense against brute-force attacks and other unauthorized login attempts.
Here’s a simplified diagram illustrating how Fail2Ban works to protect SSH:
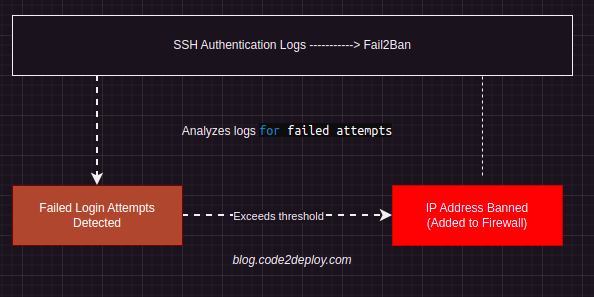
- SSH Authentication Logs: Fail2Ban monitors SSH authentication logs, which record login attempts, successful or failed, made to the SSH server.
- Analyzing Logs for Failed Attempts: Fail2Ban scans the SSH authentication logs for patterns indicating failed login attempts.
- Failed Login Attempts Detected: When Fail2Ban detects a certain number of failed login attempts from a specific IP address within a defined timeframe (as specified by the maxretry parameter), it takes action.
- IP Address Banned: Fail2Ban automatically adds the IP address that exceeded the threshold to the firewall’s blacklist, effectively banning it from accessing the SSH server.
- Enhanced Security: Banning the IP address helps prevent further malicious login attempts from that particular source, enhancing the overall security of the SSH server.
This diagram simplifies the process of how Fail2Ban operates to protect SSH, showing how it analyzes authentication logs, detects suspicious activity, and takes proactive measures to block potential threats.
Here’s a step-by-step guide on how to protect SSH with Fail2Ban:
- Installation: Begin by installing Fail2Ban on your server. Depending on your operating system, the installation process may vary. For Debian/Ubuntu systems, you can use the following command:
| sudo apt-get install fail2ban |
- Configuration: Once installed, the next step is to configure Fail2Ban to monitor SSH authentication logs. The configuration file for Fail2Ban is typically located at /etc/fail2ban/jail.conf or /etc/fail2ban/jail.local. Open this file in a text editor.
- SSH Jail Configuration: Locate the SSH jail configuration section within the Fail2Ban configuration file. By default, Fail2Ban should come with a pre-configured SSH jail. If not, you can add the following lines:
| [ssh] enabled = true port = ssh filter = sshd logpath = /var/log/auth.log maxretry = 3 |
- enabled: Set to true to enable the SSH jail.
- port: Specify the port where SSH is running. The default is ssh (port 22).
- filter: Indicates the name of the filter to be used. In this case, sshd.
- logpath: Path to the SSH authentication log file.
- maxretry: Maximum number of authentication failures before banning an IP address.
- Restart Fail2Ban: After making changes to the configuration file, restart Fail2Ban to apply the new settings:
| sudo systemctl restart fail2ban |
- Monitoring: With Fail2Ban configured, it will now monitor the SSH authentication logs for failed login attempts. If it detects multiple failed attempts from the same IP address within a specified time frame (maxretry), it will automatically ban that IP address by adding a rule to the firewall.
- Customization: You can further customize Fail2Ban to suit your specific security needs. This includes adjusting the maxretry value, setting ban durations, and configuring email notifications for bans.
By following these steps, you can significantly enhance the security of your SSH server by implementing Fail2Ban. However, it’s important to note that while Fail2Ban provides valuable protection, it should be used in conjunction with other security measures such as strong passwords, SSH key authentication, and regular software updates to ensure comprehensive protection against potential threats.
In conclusion, safeguarding your SSH access is crucial for maintaining the integrity and security of your systems. With Fail2Ban, you can proactively defend against unauthorized access attempts and mitigate the risk of security breaches. By taking proactive steps to fortify your defenses, you can better protect your valuable data and infrastructure in an increasingly hostile digital environment.